IS-3 Implementation
Overview
UC's Electronic Information Security Policy, IS-3, brings changes to the way information security risk is managed at UC, and here at UCLA. This initiative is designed to integrate IS-3's requirements and principles into UCLA's existing information security program in a way that aligns with core campus priorities and values. It will help to ensure that risk is understood and addressed at the appropriate organizational levels, and includes updating the fundamentals of the campus’ security program to current UC and industry standards.
Our Plan
As part of our multi-year program for implementing IS-3, the UCLA OCISO will roll out a comprehensive plan to enable Units to comply with their obligations under UCLA's local implementation of IS-3.
Our goal is to integrate IS-3 into UCLA’s existing information security program in a way that makes sense for campus:
- Focus on what matters most to the campus; target control implementation around supporting the mission and reducing overall risk
- Adopt systemwide policies and standards but supplement them with UCLA-specific policies, standards, and procedures as necessary
- Increased engagement, collaboration, and communication around program changes
Implementation Schedule
Phase 1:
Q3 - Q4 2022 Focus:
- Publishing Information Security Management Program
(COMPLETE)
- Roles and Responsibilities implementation and training:
(COMPLETE)
- Unit Head
- Service Provider
- Information Proprietor
- UISL
- Familiarize campus with UC Institutional Information and IT Resource Classification Standard
- Exception Process
(COMPLETE)
- UISL support rollout to Pilot Units
- Inventory Classification project kickoff
- Bruin Secure implementation
- IAM Modernization project kickoff (Discovery)
- Critical infrastructure risk assessments
Phase 2:
Winter 2023 - Summer 2023:
- Updating/developing foundational policies
- Phase 2 - IAM Modernization project (Design and Implementation)
- Privilege access management
- AD Consolidation
- IGA solution determination and implementation
- Implementation of campus inventory classification platform
- Pilot unit onboarding into the platform
- Rollout Unit onboarding kits
- Rollout campus risk management methodology to campus units
- High-level IS-3 assessment for Pilot Units
Phase 3:
Fall 2023 Focus:
- Onboard second cohort of Pilot Units
- UISL assignment
- High-level IS-3 assessment
- Inventory and classification of assets
What Units Can Do Now:
Campus-level implementation of IS-3 will take multiple years. However, there are things that Units at all levels can do to get started.
Roles and Responsibilities
Familiarize yourself with the roles and responsibilities identified in IS-3 through our IS-3 training and Awareness presentation. This presentation provides a high-level overview of the critical roles and responsibilities outlined in IS-3. Identified roles include Unit Heads, Unit Security Leads, Information Proprietors, Service Providers, Workforce Managers, and Workforce Members. Learn even more at the UCOP Quick Start Guide(link is external).
- Identify your Unit Head and Unit Information Security Lead(s). These people have key roles in IS-3.
- Identify any IT Services that your Unit provides. Many of the Service Provider responsibilities in this policy are not new, but were previously divided among several policies. Service Providers may benefit from this consolidated list of responsibilities.
Familiarize yourself with UC Protection Levels
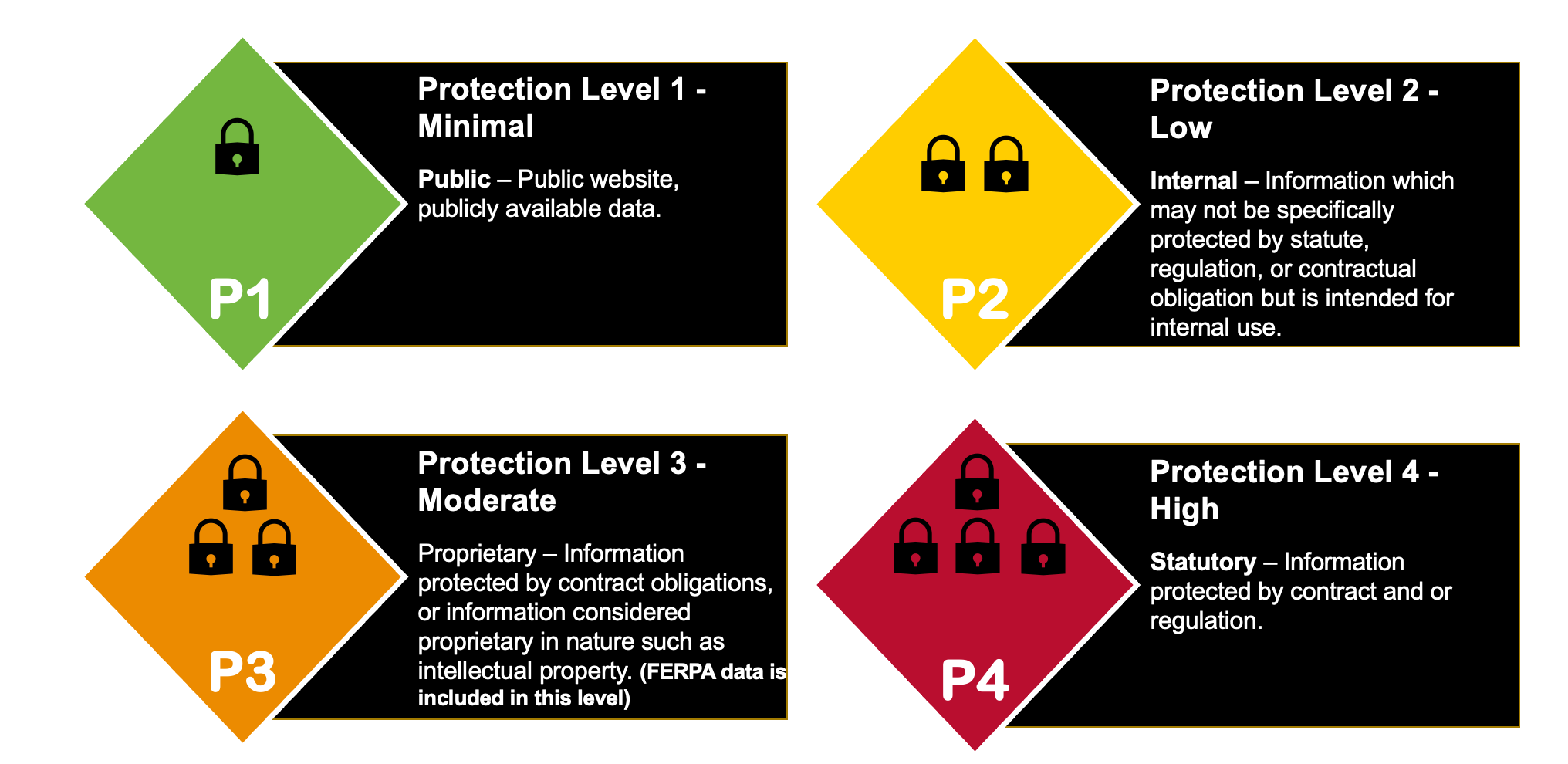
UC Institutional Information and IT Resources are classified into one of four Protection Levels (P1-P4) based on the level of the impact associated with the compromise of the asset or the institutional information which is processed, stored, or transmitted by the asset. P4 requires the most security controls, and P1 requires a minimal set of controls. The four Protection Levels are described in the UC Data Classification Standard and Guide)(link is external) and in the graphic below.
Learn about the new Availability Levels
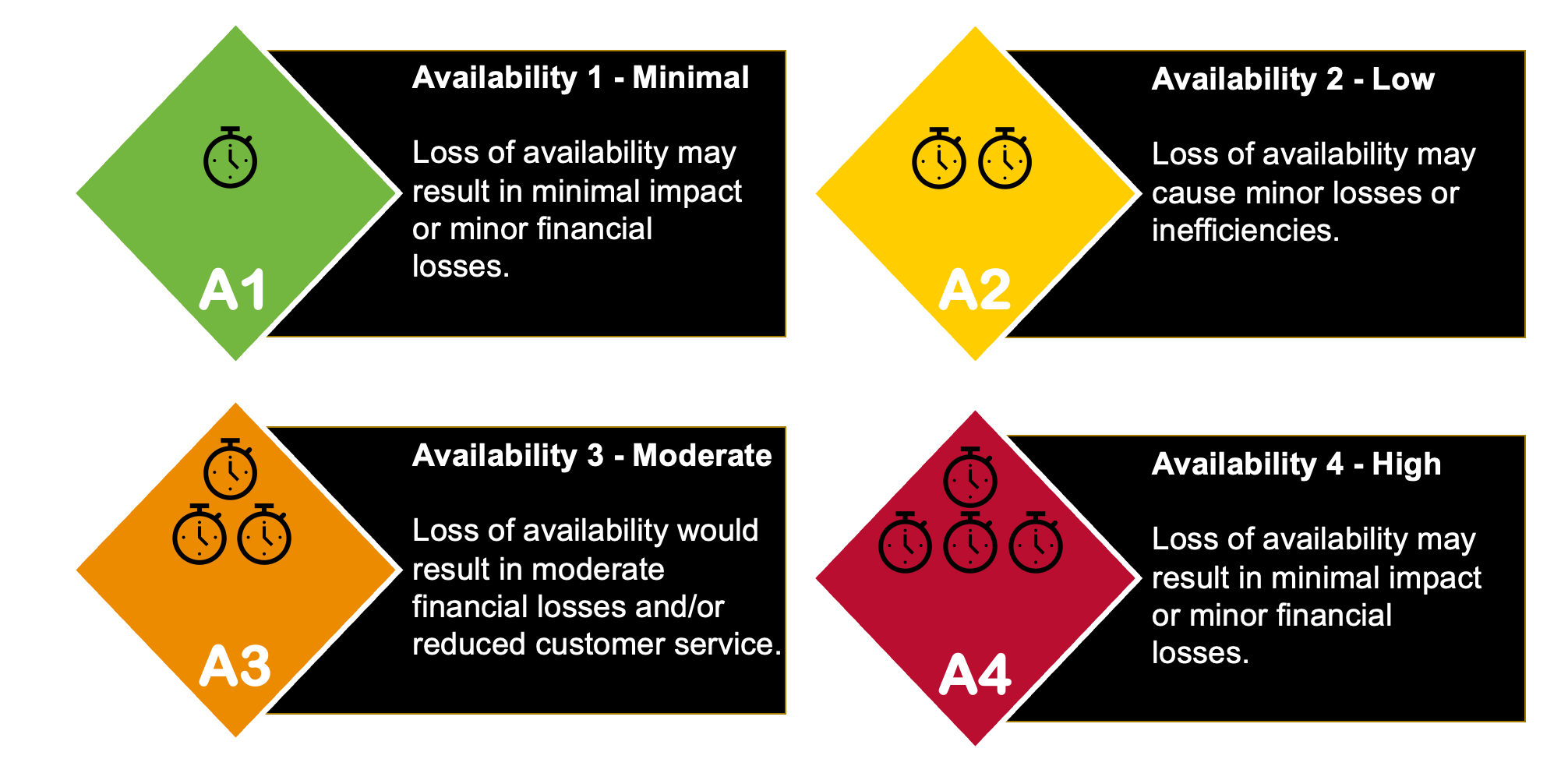
This is a new concept for information security at UC. Availability Level refers to the impact of the loss of availability of the data or service, measured on a scale of 1-4. A4 is the highest level of impact, and A1 is the lowest. Availability Level helps to determine what protections are required to ensure that information and resources are available when needed. The four Availability Levels are described in the UC Data Classification Standard and Guide)(link is external) and in the graphic below.
Identify and classify your Unit's Institutional Information and IT Resources
- Work on bringing your IT assets into compliance with UC’s current minimum security standards. IS-3 will build on these, so this is an excellent place to start:



